Threat Intelligence and The Pyramid of Pain
€ 38.00 · 5 (660) · In Magazzino
Di uno scrittore di uomini misteriosi

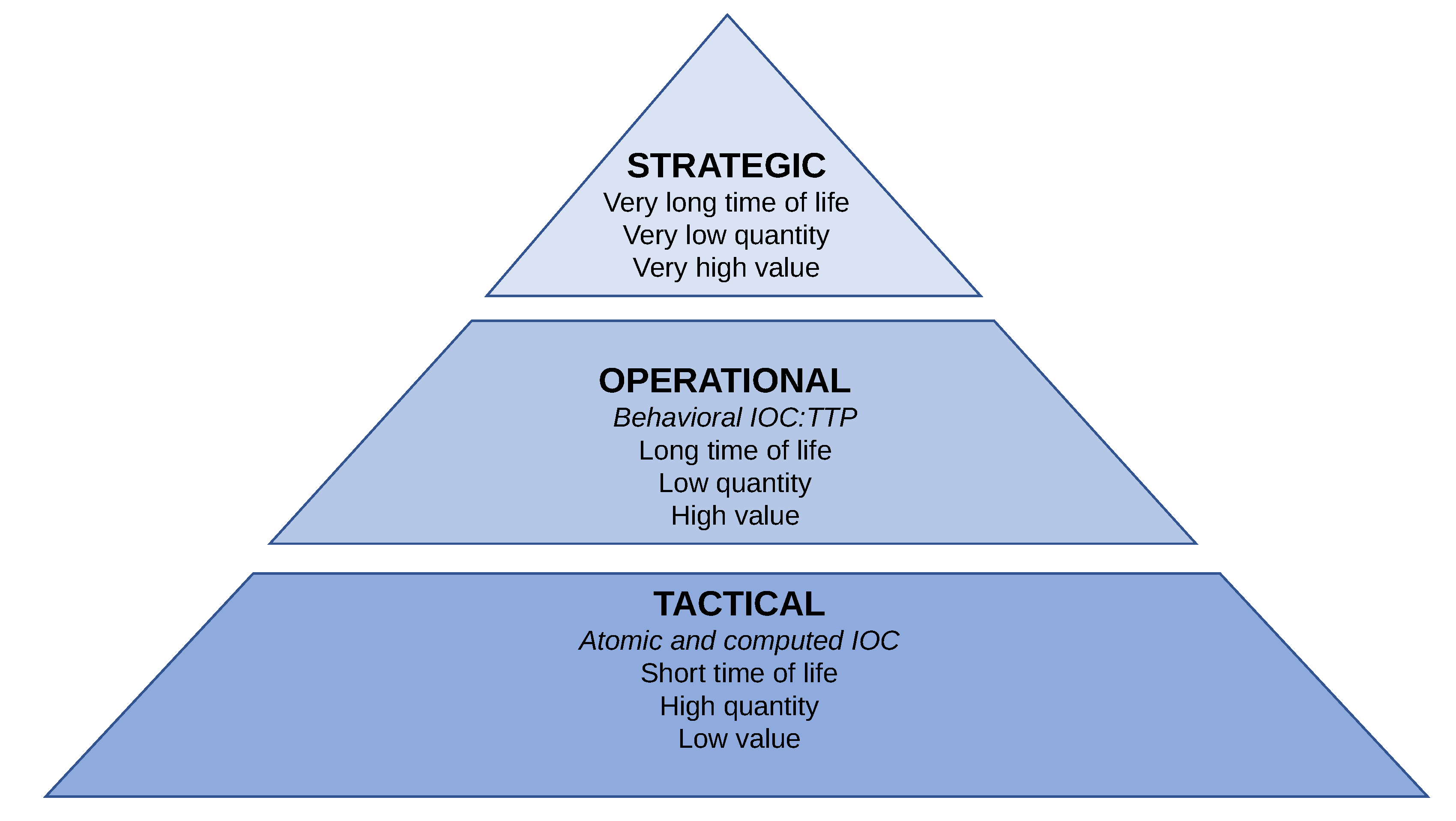
There is great interest among security technology and service providers about the intersection of global threat intelligence with local observations in the network. While there is certainly cause for excitement, it’s worth pausing to ask the question “Is Threat Intelligence being used effectively?”
Electronics, Free Full-Text

Threat Hunting Techniques: A Quick Guide

APNIC on X: Cyber threat intelligence sharing – ascending the pyramid of pain, one of our #top3 #cybersecurity posts for 2016 / X
EC-COUNCIL on X: David Bianco's #PyramidOfPain lists six indicators of cyberthreats, plus how much pain it causes an adversary when their plans are thwarted at each level. Sign up for the #CTIA

Summiting the Pyramid of Pain

Cisco Security Alignment to the Pyramid of Pain: Part 1 The Overview

What You Need To Know About The Pyramid of Pain – Cyberwarzone
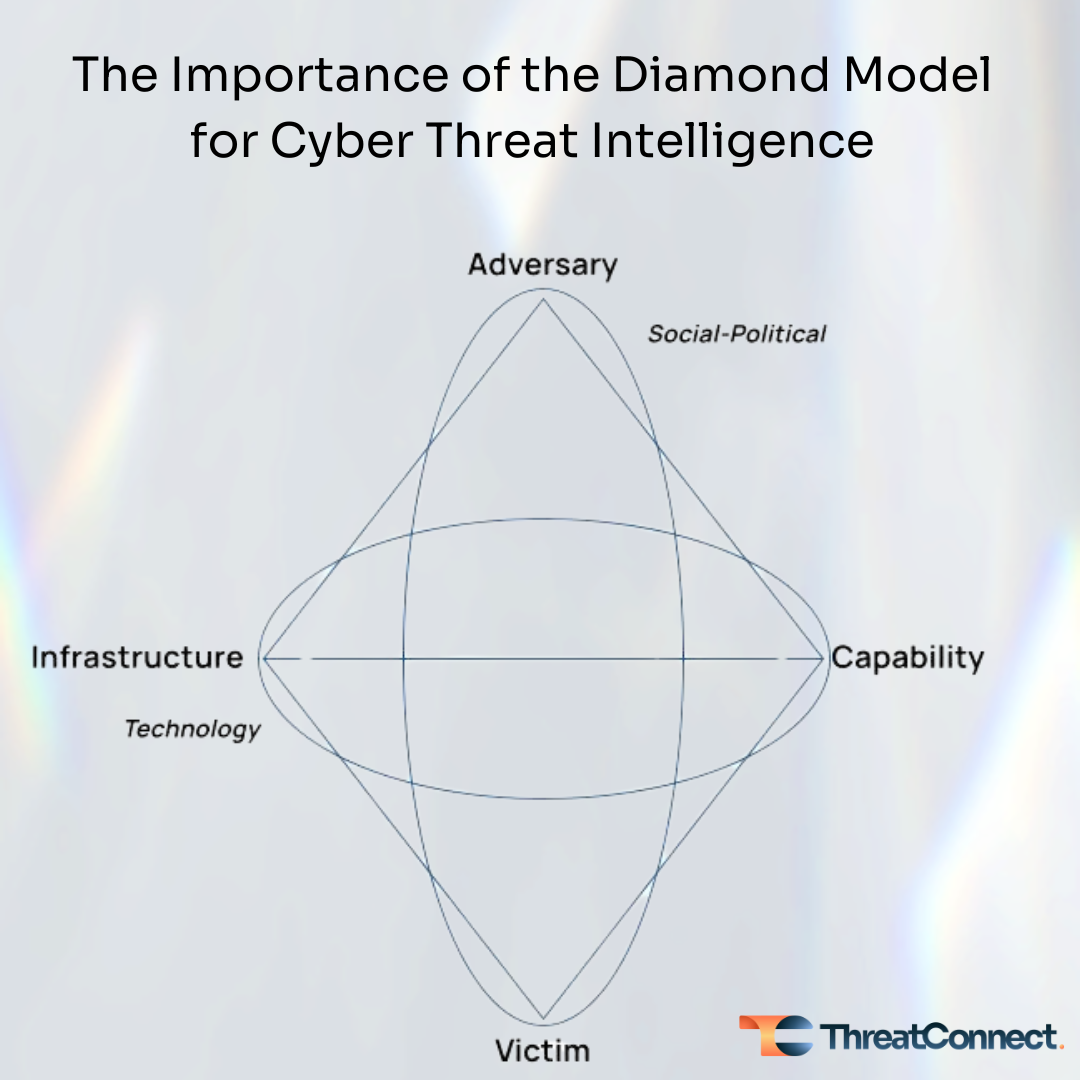
The Importance of the Diamond Model for Cyber Threat Intelligence
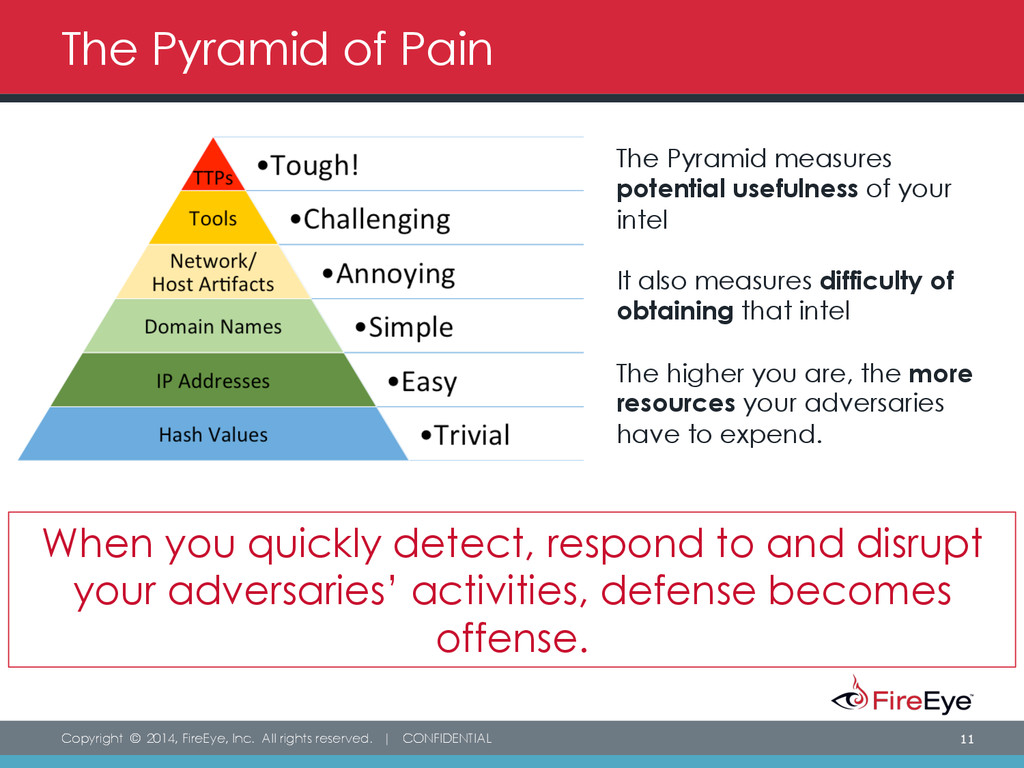
The Pyramid of Pain: Intel-Driven Detection & Response to Increase Your Adversary's Cost of Operations - Speaker Deck
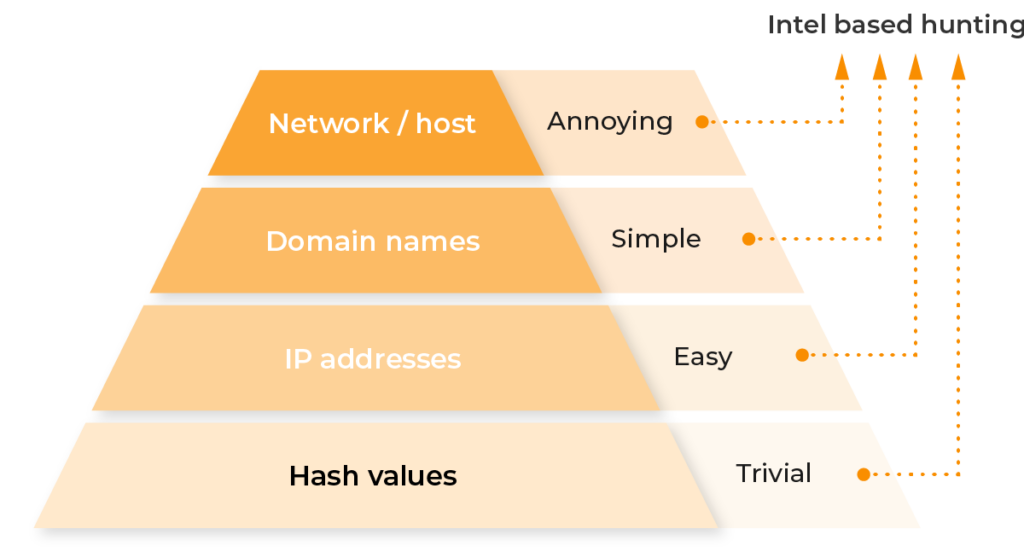
How Lumu Enables Threat Hunting
The Pyramid of Pain
What Is Pyramid of Pain?
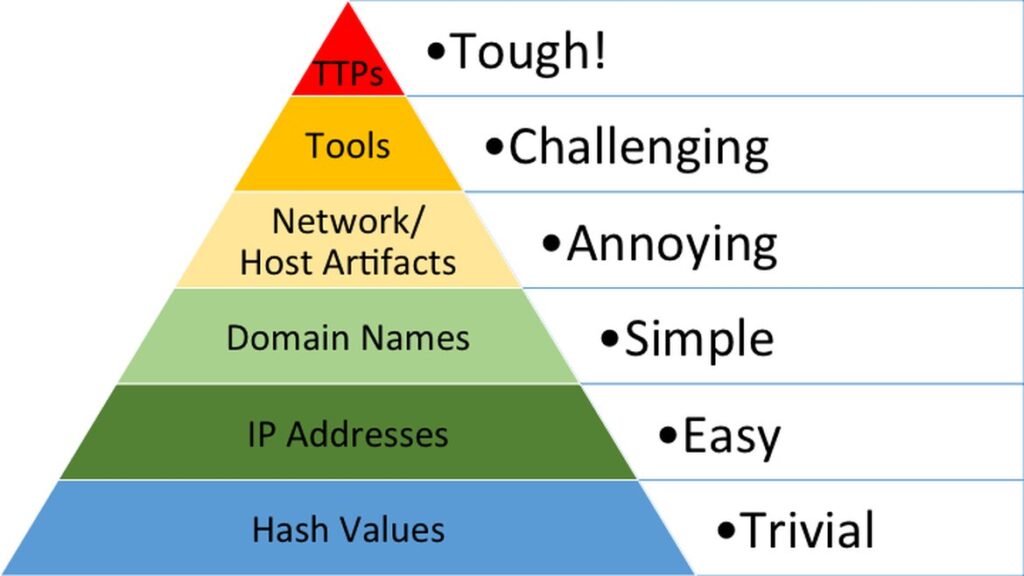
Pyramid of Pain - AttackIQ
MITRE ATT&CK and How to Apply It to Your Organization

Re-examining the Pyramid of Pain to Use Cyber Threat Intelligence More Effectively - SOCRadar® Cyber Intelligence Inc.

